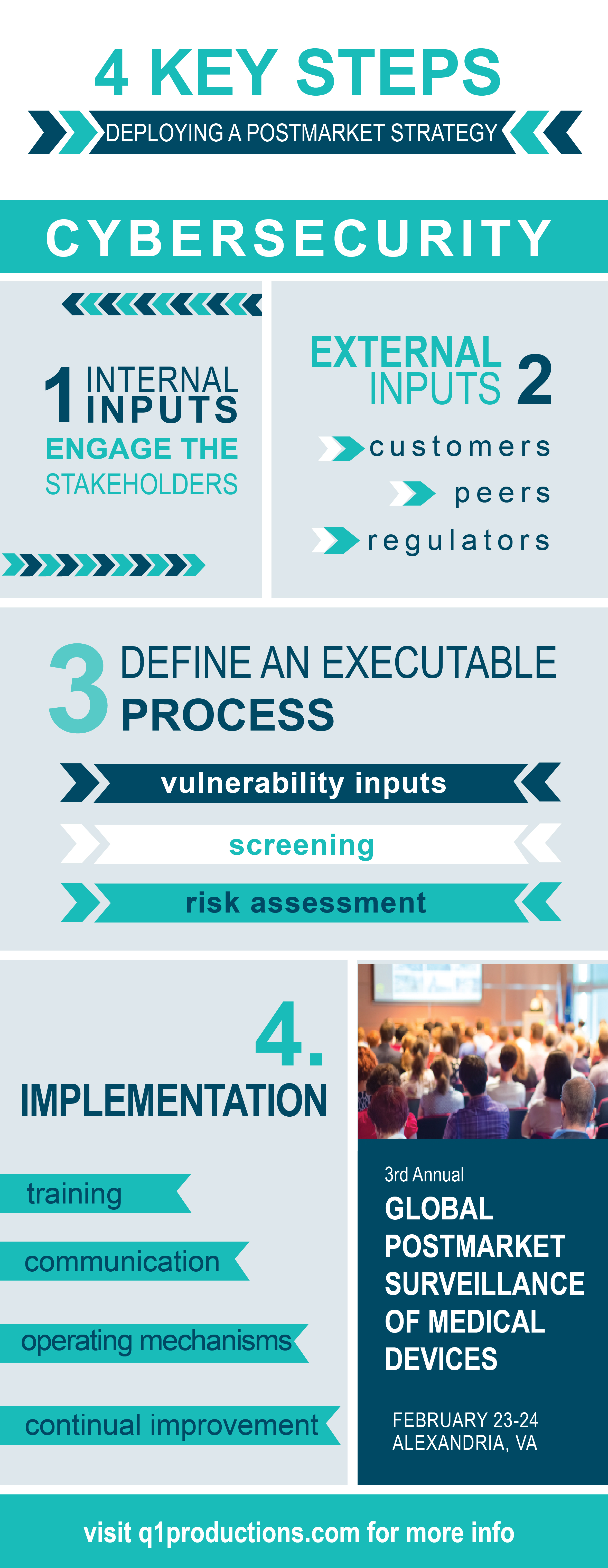
4 Steps to Deploy a Cyber Security Postmarket Strategy
While the development of innovative technologies and connected devices continues to flourish, public concern surrounding cyber security has increased significantly in recent years. With various news stories breaking about hackers and system failures due to cyber security breaches, the recognition of a potential cyber security risk in medical devices is at an all-time high. In many cases, devices that are currently being used across the country, and around the world, were designed before cyber security was top of mind. Now these devices are operating in an environment where there are risks present that they were not designed to meet.
The medical device industry has to adapt to older devices, with long life-cycles, encountering emerging threats. I spoke with Steven Abrahamson, Director of Product Security Engineering and Privacy at GE Healthcare, about some of the mechanisms and steps he uses to identify risks, and how to appropriately deal with them. “We have to make sure we are looking at it rationally, and recognizing what the risks really are” explained Steven Abrahamson, a speaker at this year’s Global Postmarket Surveillance of Medical Devices Conference. “There are various things we can do to monitor what the threat level and activity levels are in the field, so we don’t expend resources addressing risks that may not be significant.”
The following four steps, defined by Steven Abrahamson, outline how to most efficiently deploy a cyber security postmarket strategy.
Internal Inputs: Engage Stakeholders
It’s very important to make sure you aren’t viewing cyber security purely as an engineering issue. Ideally, start with a central product cyber security team that can work closely with the people in engineering, regulatory, legal, supply chain, service, sales, product management, and others to plan a comprehensive strategy addressing emerging cyber security concerns.
When handling specific vulnerabilities, there is always a lot of information available. Many different vulnerabilities can be identified internally, and each has an effect on a different type of product or device. It is important to assess which vulnerabilities pertain to your specific devices, as there are many that don’t have a significant impact on medical devices, given how they are used and the environment that they are used in.
There should be a mechanism in place to translate the external information into information that can be used internally to assess the risk in devices. As well as the full engagement of everyone involved in managing risks in your product portfolio across the business.
External Inputs: Consumers, Industry Peers, Regulators
The industry is constantly working on good mechanisms to share information externally. An effective environment for sharing information on risks and vulnerabilities with industry peers, regulators and consumers is extremely important. The extent of which information can be shared on vulnerabilities, threats, and potential ways to address the associated risks, can help minimize risks in the ecosystem.
Define an Executable Process: Vulnerability Inputs, Screening, Risk Assessment
“If a process is not executable it doesn’t do anyone any good” explained Abrahamson. There are many identifiable vulnerabilities out there, so it is important to translate them into a list that is actionable by the product engineering team. For example, if you have a list of a thousand vulnerabilities that may affect the device, a manufacturer is not going to know what to do with that. You have to put in place a mechanism to identify which vulnerabilities are potentially impactful. From there you can work with the engineering team to create a process that determines what the risk level is, and where you have to take action.
While this is important make an actionable plan with any manufacturer, when dealing with a larger manufacturer, that might have hundreds of products and tens of thousands of devices, you have to really consider scale-ability. Anything that makes sense at an individual venerability level must be scaled to hundreds of vulnerabilities on tens of thousands of devices.
Implementation: Training, Communication, Operating Mechanisms, Continual Improvement
When it comes to implementation, anything you do must be viewed as part of a system. Cyber security is an area that many medical device manufacturers, and people within the manufactures organizations, are not familiar with. As you implement new practices to address risks, it is important to make sure people understand what they are, have clear definitions of the processes, and go through a formal implementation. Like any well-executed system, training, communication, and operating mechanisms are key elements to ensure a smooth transition.
A cyber security system is very analogous to a quality system. The approach that can be taken in a quality system can also be translated when looking at security requirements. There has to be a mechanism in place to measuring effectiveness, and continual improvement.